Help Prevent Hacking with 2-step-verification:
Hacking and phishing scams are in the news daily. One way to prevent email hacking is to use 2-step verification. Here is how to set up 2-step verification for 3 of the most popular email systems: Google, Microsoft and Apple.
Google 2-Step Verification Support Page:
- Go to the 2-Step Verification page. You might have to sign in to your Google Account.
- Select Get started.
- Follow the step-by-step setup process.
Once you’re finished, you’ll be taken to the 2-Step Verification settings page. Review your settings and add backup phone numbers. The next time you sign in, you’ll receive a text message with a verification code. You also have the option of using a Security Key for 2-Step Verification.
Microsoft Two Step Verification Support Page:
Two-step verification helps protect you by making it more difficult for someone else to sign in to your Microsoft account. It uses two different forms of identity: your password, and a contact method (also known as security info). Even if someone else finds your password, they’ll be stopped if they don’t have access to your security info. This is also why it’s important to use different passwords for all your accounts.
You set up two-step verification with an email address, phone number, or authenticator app. When you sign in on a new device or from a new location, we’ll send you a security code to enter on the sign-in page.
If you turn on two-step verification, you’ll get a security code to your email, phone, or authenticator app every time you sign in on a device that isn’t trusted. When it’s turned off, you will only have to verify your identity with security codes periodically, when there might be a risk to your account security.
If you turn on two-step verification, you will always need two forms of identification. This means that if you forget your password, you need two contact methods. Or if you lose your contact method, just your password won’t get you back into your account. For that reason, we strongly recommend you keep three pieces of security info on your account, just in case.
To turn two-step verification on or off
- Go to the Security settings page, and sign in with your Microsoft account.
- Under Two-step verification, choose Set up two-step verification to turn it on, or choose Turn off two-step verification to turn it off.
- Follow the instructions.
Apple Two Step Verification Support Page:
It requires you to verify your identity using one of your devices or another approved method before you can:
- Sign in to your Apple ID account page
- Sign in to iCloud on a new device or at iCloud.com
- Sign in to iMessage, Game Center, or FaceTime
- Make an iTunes, iBooks, or App Store purchase from a new device
- Get Apple ID-related support from Apple
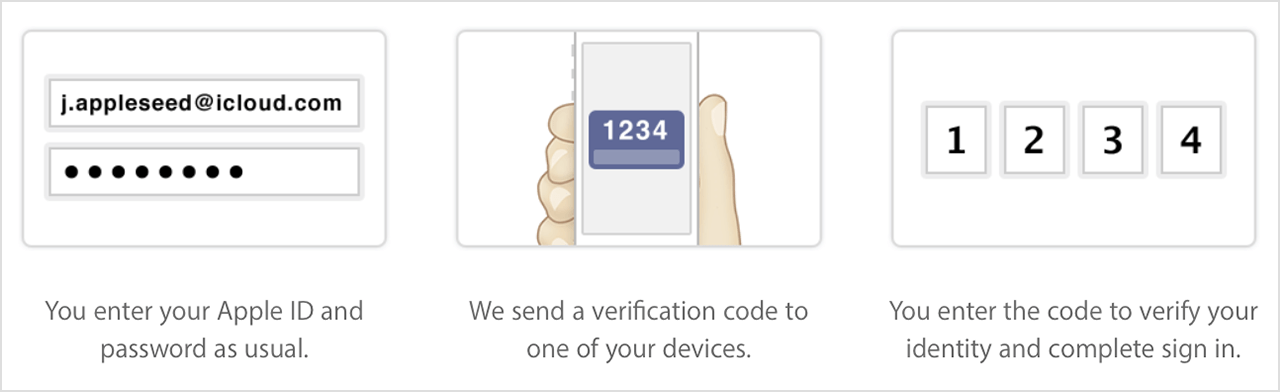
After you sign in, you can securely access your account or make purchases as usual. Without both your password and the verification code, access to your account is denied.
You’ll also get a 14-character Recovery Key to print and keep in a safe place. Use your Recovery Key to regain access to your account if you ever lose access to your trusted devices or forget your password.




